Information Security Training

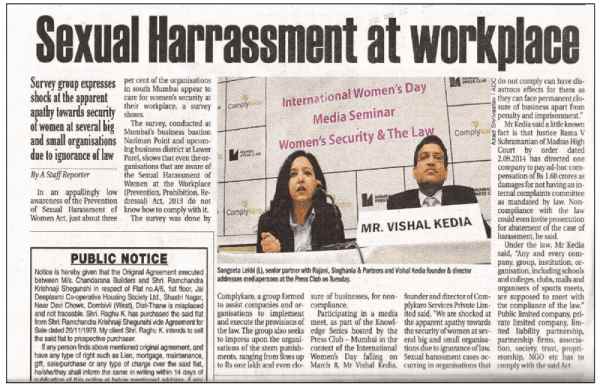
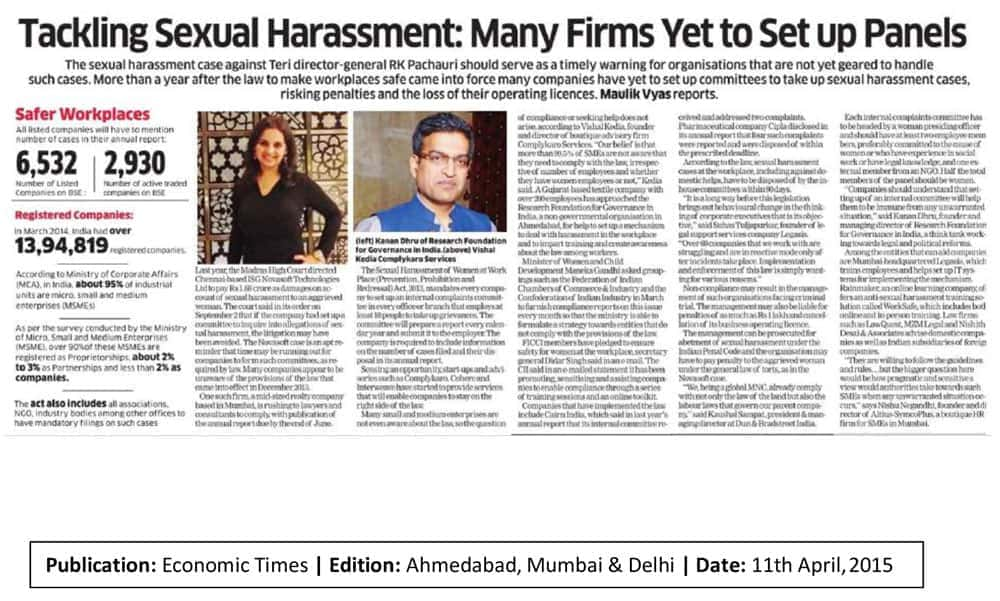
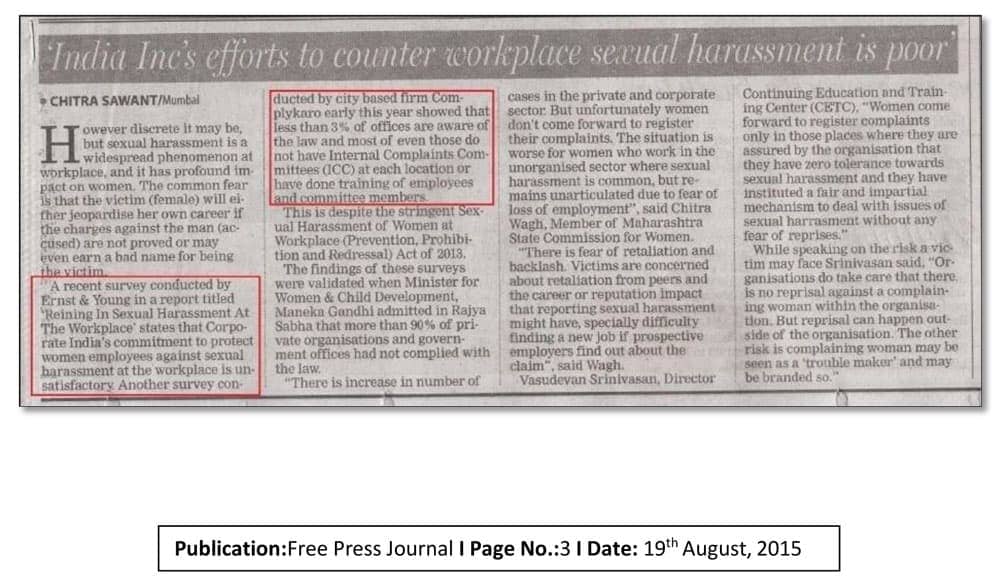
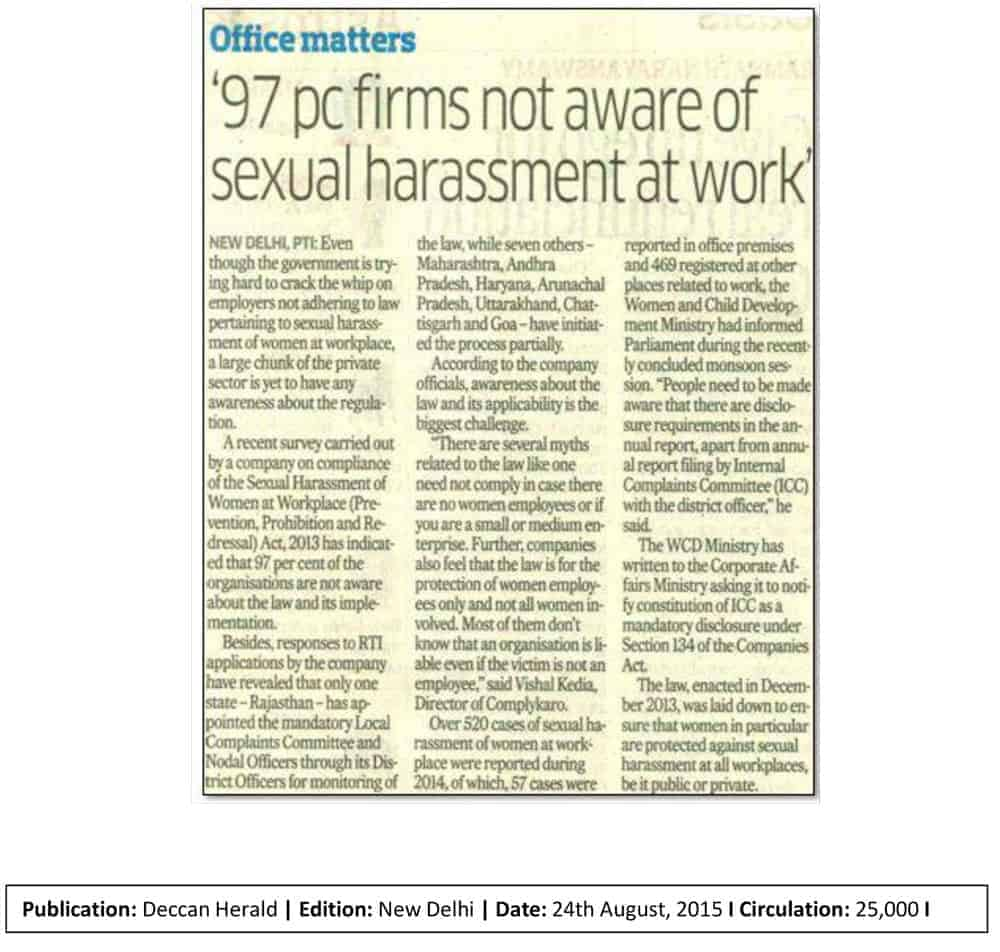
Companies use data storage mediums to store all their data for easy access and feasibility. While data storage and usability have simplified monotonous processes, they have also made cybersecurity an absolute necessity. A company needs to provide information security training to its employees for technicalities and their ethical duties regarding the company’s cybersecurity. It is required to ensure cybersecurity in order to avoid unlawful access & usage of a company’s data.
Through our online information security awareness training for employees, we assist your company to comply with your organisation’s information security policies seamlessly by creating awareness amongst employees to operate ethically.
Information Security Training
Our information security training for employees incorporates the following topics in detail:
 The need and means to set up systems that grant or deny data access to different people or teams.
The need and means to set up systems that grant or deny data access to different people or teams.- Ways to keep track of all the different passwords and keeping them safe.
- Concept, importance, and technique of Encryption management.
- Classification and handling of all kinds of company data.
- Ways to keep the company’s data intact in case of any IT service disruption.
- Using anti-virus software – protecting the company’s data on every device by using anti-virus software.
- Intellectual property rights.
- Awareness of any data-related association of the third party ensures security and avoids any leak.
FOR MORE DETAILS ABOUT INFORMATION SECURITY TRAINING
Benefits of Information Security Course


Data Security
Our Information Security program training will help your employees in ensuring any loss or unlawful access to your company’s precious data.


Facilitates Compliance
By educating employees about the necessity of handling the company’s data with the utmost care and the means to do it, our Information Security training will help your company comply with the law and employees maintain an ethical stance.


Reputational Risk Management
The security breach of a company’s data makes it extremely vulnerable to legal issues, and the brand may lose face. Complykaro’s Information Security training prepares your employees to avoid such situations and keeps your brand image intact.
Choose Us?

Interest Provoking Course
By the end of our Information Security course, the attendees will be well-versed with every aspect of it without being subjected to boredom.

24 x 7 Support
We provide round-the-clock support to our clients to address all of their concerns and queries.

Customisable Training Programs
Personalised to suit our clients’ Organisational requirements, we tailor-make extensive courses.

Comprehensive Programs
The courses we offer are interactive with scenario-based assessment throughout to ensure absolute understanding.

Easy Access to Programs
Since our Information Security course is available on our cloud-based E-learning platform, it can be easily accessed online to suit your time and comfort.

Legally Curated Courses
All our courses are curated with absolute legal accuracy. At the end of the course, your employees will be well-versed with their duties and responsibilities, ensuring compliance.

Cost-Efficient Solutions
By offering scalable solutions, Complykaro ensures that Organisations of all sizes can access cost-efficient compliance training services. This affordability makes it an accessible choice for a wide range of businesses.

Certification
Get certified on completing our Information Security training program.

Seasoned Team
Our team of dedicated professionals with 75+ years of combined experience Utilise the best means of creating and conducting interactive and elaborate Information Security modules.
FOR MORE DETAILS ABOUT INFORMATION SECURITY TRAINING
Video
Complykaro's Information Security Training
With digitization of data, it is important for you employees to understand their duties and responsibilities regarding information security. It is required, by law, to ensure cybersecurity in order to avoid unlawful access & usage of a company’s data.
With our Information Security awareness training, we assist your company to comply with the law and employees to operate ethically.
Services

Assisting your firm in complying with the Prevention of Money Laundering Act by enhancing employees’ understanding of money laundering & illicit transactions.
Read More

Encouraging your employees identify and avoid discrimination against specially-abled persons and help your organisation comply with the RPWD Act.
Read More

Training employees through E-Learning to operate ethically and abide by the company’s code of conduct.
Read More

Creating an inclusive workplace in your organisation by desensitising employees towards the transgender community and complying with the corresponding act.
Read More
Download Our E-Brochure
Answer to Your Questions
Information security training refers to awareness training solutions that equip employees with the knowledge and skills to act ethically when it comes to information security. This is essential for organisations to protect data and prevent cyberattacks.
Information security training is for every person in an organisation, regardless of their seniority or status. Cyber attackers can target anyone, regardless of their status in the organisation.
Yes, Complykaro’s information security training is available online through our platform to make it accessible for all. If you would like to have an information security training for your organisation, contact us today.
Yes, we provide a certificate upon completion of the information security training.
Yes, we also conduct instructor-led training on the said topic either in person or through webinars. These are conducted exclusively by our founder & expert trainer, Mr. Vishal Kedia.























 Rishab is a seasoned professional with over 9 years of invaluable hands-on experience in client-facing roles that span his career. His expertise lies in cultivating successful strategic partnerships that benefit all stakeholders. With a keen aptitude for organizational management, Rishab excels at fostering enduring client relationships. His dedication centers around enhancing Complykaro’s visibility and brand esteem. At Complykaro, Rishab spearheads pivotal responsibilities, including business development, strategic planning, and operational excellence.
Rishab is a seasoned professional with over 9 years of invaluable hands-on experience in client-facing roles that span his career. His expertise lies in cultivating successful strategic partnerships that benefit all stakeholders. With a keen aptitude for organizational management, Rishab excels at fostering enduring client relationships. His dedication centers around enhancing Complykaro’s visibility and brand esteem. At Complykaro, Rishab spearheads pivotal responsibilities, including business development, strategic planning, and operational excellence.